5. Windows Log Analysis: Determine Compromised System¶
Difficulty: 🎄🎄
Determine Attacker Technique
The attacks don't stop!
Can you help identify the IP address of the malware-infected system using these Zeek logs?
For hints on achieving this objective, please visit the Laboratory and talk with Sparkle Redberry.
⚡️ Solution¶
After completing Xmas Cheer laser Challenge and talk to Sparkle Redberry , He will give you hints which will help you with this objective:
RITA
Watch | RITA - Finding Bad Things on Your Network Using Free and Open Source Tools
RITA - Finding Bad Things on Your Network Using Free and Open Source Tools
Watch | Tech Segment: RITA with John Strand - Enterprise Security Weekly 55
Tech Segment: RITA with John Strand - Enterprise Security Weekly #55
-
Unzip Zeek logs file.
-
Open
elfu-zeeklogs/ELFU/index.htmlfile in your browser. -
Select
ELFUdatabase:
-
Select
Beaconfrom top menu to search for signs of beaconing behavior in and out of the network:
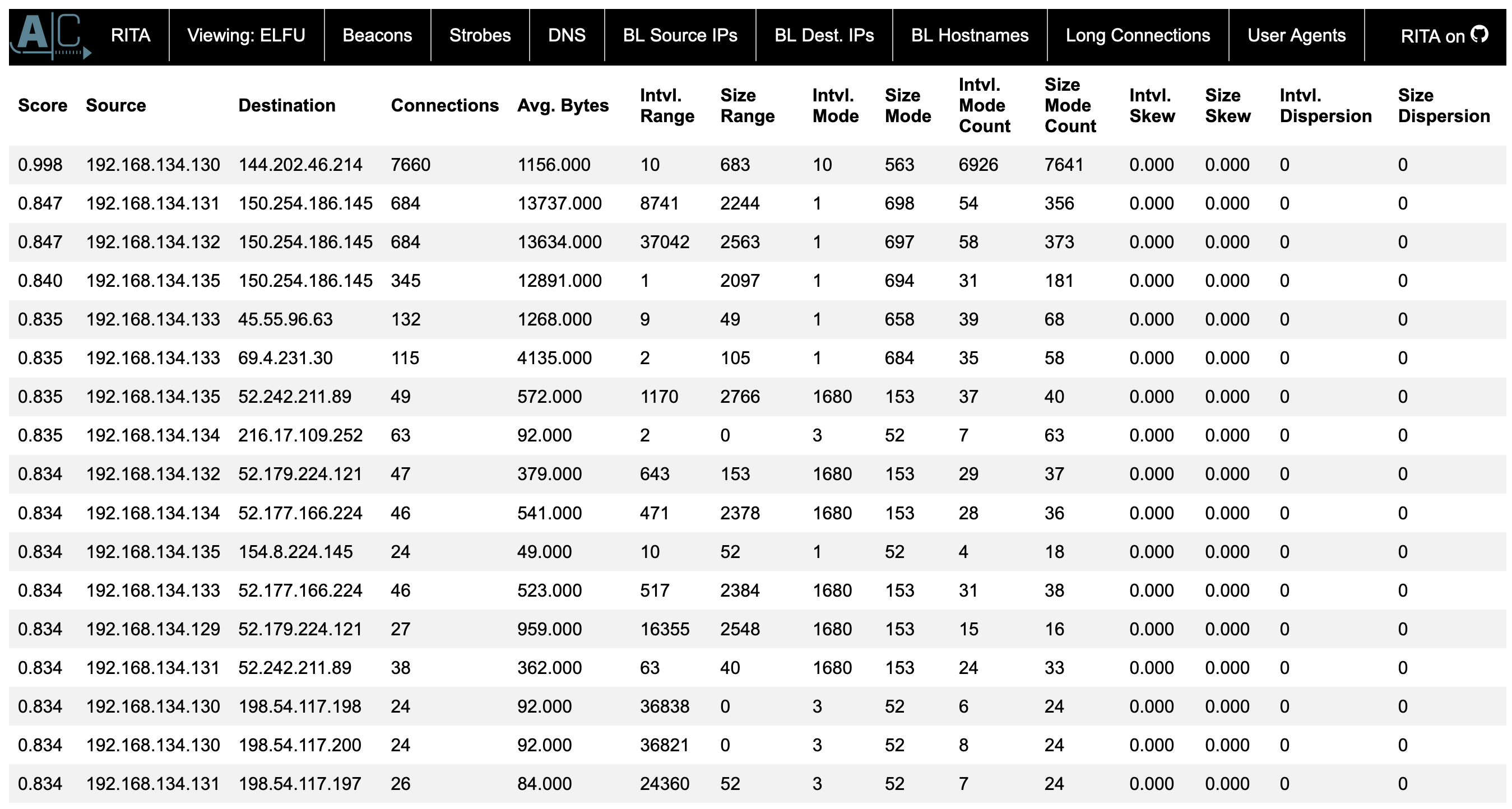
You can see that we have one system that has almost a perfect score for beacon. Also we have 7660 different connections that are being made that is a lot of almost a perfect beacon.
Score Source Destination Connections 0.998 192.168.134.130 144.202.46.214 7660 We can also look at longer connection you can the same source ip address at the top with longest connection duration.
Source Destination DstPort:Protocol:Service Duration 192.168.134.130 148.69.64.76 443:tcp:-, 443:tcp:ssl 1035.9001 The IP address of the malware-infected system is
192.168.134.130.The answer:
192.168.134.130
Congratulations! You have completed the Network Log Analysis: Determine Compromised System challenge! 🎉
🎓 What you've learned¶
- Using RITA framework for network traffic analysis.
- Signs of beaconing behavior in and out of the network.